When you look at the mission statement of OpenSource Science, you will discover it's all about the freedom of people and the sustainability of open source technology. We were founded because students leaving traditional technological universities know zero to nothing about open source technology, but nevertheless, have a diploma in Computer Science. When you consider that 95% of the Internet runs on #foss this is very hard to comprehend.
But now, back to education, OS-SCi educates using problem-based learning, which differs from traditional learning, in a way that we try to give the students a real motivation to learn. They are not studying the material because we say so, but they are looking at the study material for solutions to their problem.
The exercises are designed in such a way that they will trigger questions, so the students will learn. In a way, problem-based learning has a basis in biology. When you watch young animals with their mothers, you always see a mother who watches when the puppies learn. The kids learn through experience. There are no instructions in advance.
When we are talking about traditional education and a professor speaking to a group of students, it's too fast for some students and too slow for others. We offer the students adept material in video and writing to study and to use to find solutions to the problems they have to solve.
Lets look at an example from our second Python course.
During the Second World War, the Germans created two magical encryption machines to secretly communicate with a cipher script. Both machines were based on the algorithms developed by Gilbert Vernam (1919).
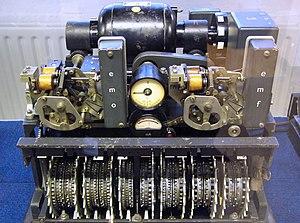
The Lorenz SZ42, a machine used by the Nazi's in WOII to encrypt and decrypt messages, based on the Vernam algorithm
Gilbert
Sandford Vernam
April 3, 1890 – February 7, 1960 was
a Worcester Polytechnic Institute 1914 graduate and AT&T Bell
Labs engineer who, in 1917, invented an additive polyalphabetic
stream cipher and later co-invented an automated one-time pad cipher.
Vernam proposed a teleprinter cipher in which a previously prepared
key, kept on paper tape, is combined character by character with the
plaintext message to produce the ciphertext. To decipher the
ciphertext, the same key would be again combined character by
character, producing the plaintext. Vernam later worked for the
Postal Telegraph Company, and became an employee of Western Union
when that company acquired Postal in 1943. His later work was largely
with automatic switching systems for telegraph networks.
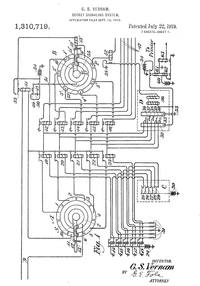
Vernam's
patent
The combining function Vernam specified in U.S.
patent 1,310,719, issued July 22, 1919, is the XOR operation, applied
to the individual impulses or bits used to encode the characters in
the Baudot code. Vernam did not use the term "XOR" in the
patent, but he implemented that operation in relay logic. In the
example Vernam gave, the plaintext is A, encoded as "++---"
in Baudot, and the key character is B, encoded as "+--++".
The resulting ciphertext will be "-+-++", which encodes a
G. Combining the G with the key character B at the receiving end
produces "++---", which is the original plaintext A. The
NSA has called this patent "perhaps one of the most important in
the history of cryptography."
Vernams Patent
The basis of this algorithm is a exclusive or (XOR) addition with a pseudorandom generated stream of bits.
In the example below you see an original message (org) with a pseudo random bitstream. Both bit ranges are calculated using a logical XOR. This results in an encoded message.
On the receiving part, the receiver uses the XOR calculation with the same pseudo bitstream on the encoded message to decode, and the original message is recovered.
This is the most complicated exercise until now, for which you also might need other sources. This exercise leans on our concept of problem based learning. You will run into obstacles you need to solve. Ask your peers and professor with concrete questions.
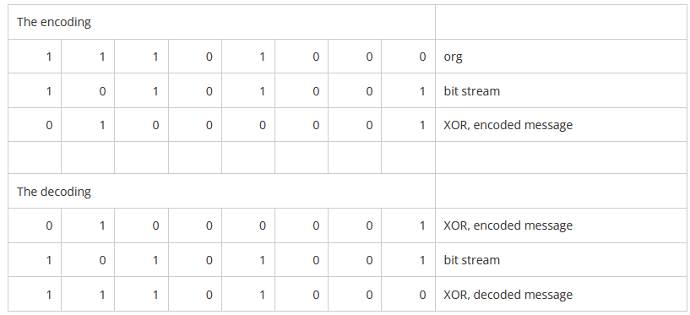
XOR example
Create an application which uses this technology to encrypt and decrypt a String.
As you can see in the exercise, the students are enticed by a real interesting problem that left its traces on the human history. The students will start watching videos, reading in books, talking to their professors and peers and try several solutions, before they crack the problem and build the algorithm. The knowledge and experience they gain will be cemented in their brains.